Migrating your Applications from Public/Private Environment to Azure Stack
Microsoft Azure Stack is a Hybrid Cloud platform that offers capabilities of both, Private Cloud and Azure Public Cloud. If you want to deliver Azure services from your organization’s private environment without compromising on the security standards implemented in your private environment, you can migrate to Azure Stack Cloud.
You might have to assess the feasibility of migrating the servers to suitable Cloud resources in Azure Stack. The actual migration of servers from your private environment to your Azure Stack Cloud poses a different challenge since you might have to provide access to the Cloud Migration Services available outside your environment.
Private environment restricts access to servers for outside entities. MaaS Private Solution offers a feasible and tailor-made solution for migrating to Azure Stack from a private environment.
Solution Overview:
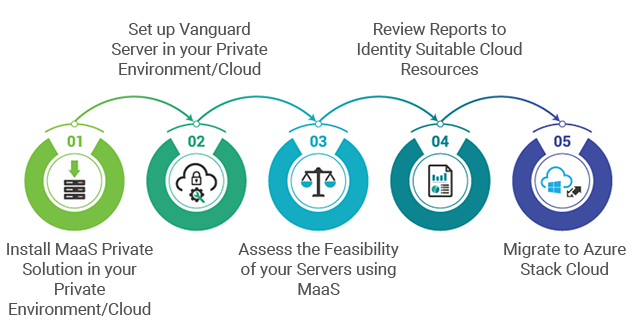
Solution:
MaaS Private Solution will be downloaded and installed in one of the servers in the private environment. It independently operates without internet to ensure data safety. You can customize the MaaS Cloud Knowledgebase by updating it with your Azure Stack flavor configurations which will be used during Cloud compatibility analysis.
MaaS Private Solution (Azure Stack) Workflow:
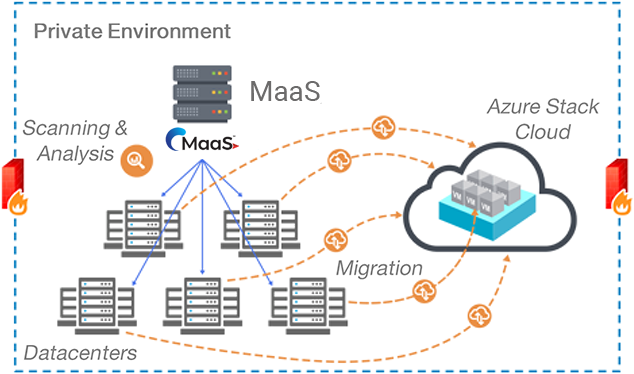
Scanning and analysis of application/infrastructure servers can be performed in 2 different modes – agent scan and agentless scan – and can migrate the application to your Azure Stack Cloud.
Agent scan requires the MaaS agents to be installed in all servers, whereas the agentless scan requires the MaaS agent to be installed only in the server where the MaaS Private Solution is installed.
MaaS Private Solution requires internet connection to migrate the servers during Cloud migration only if the Azure Stack Cloud is set up outside your private environment.
Conclusion:
Using MaaS Private Solution, application/infrastructure servers from your private environment can be migrated to your Azure Stack Cloud without compromising on data security while adhering to your unique business requirements.

